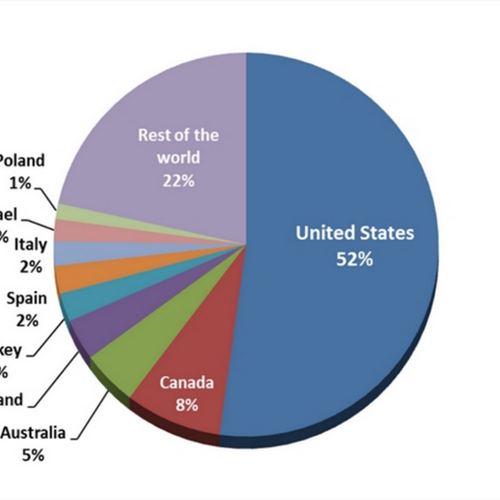
Ransomware, or crypto-extortion, is making a strong resurgence. In December 2013, ESET Security determined that ransomware belonging to the nefarious CryptoLocker family has propagated to every corner of the world. And more than 50 percent of the attacks were happening right here in the United States.
Source: ESET Security
Even though CryptoLocker is a highly successful piece of malware, it appears it's about to be usurped by an even more insidious ransomware called PowerLocker.
What Is Ransomware?
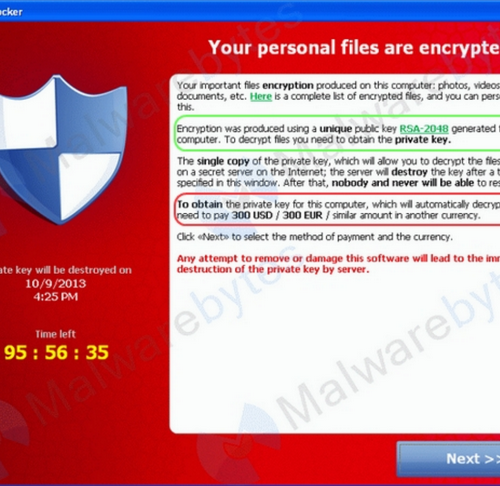
For those not familiar with ransomware, now is the time to learn about it. In fact, it's much better to read about it now, than be introduced to it via a sinister-looking window like the one below.
Source: Malwarebytes.org
The slide is advertising that ransomware, in this case CryptoLocker, has taken over the victim’s computer. Malwarebytes.org has determined that CryptoLocker searches for files with the following extensions:
3fr, accdb, ai, arw, bay, cdr, cer, cr2, crt, crw, dbf, dcr, der, dng, doc, docm, docx, dwg, dxf, dxg, eps, erf, indd, jpe, jpg, kdc, mdb, mdf, mef, mrw, nef, nrw, odb, odm, odp, ods, odt, orf, p12, p7b, p7c, pdd, pef, pem, pfx, ppt, pptm, pptx, psd, pst, ptx, r3d, raf, raw, rtf, rw2, rwl, srf, srw, wb2, wpd, wps, xlk, xls, xlsb, xlsm, xlsx
Some of the more familiar extensions, found in bold, are related to Microsoft Office documents. If the victim had documents with any of the above extensions on their now-infected computers, the files would become completely inaccessible. In other words, they will be held ransom.
In the screenshot above, the section circled in green mentions that public-private key encryption was used to encrypt the files. And, unless you work for the NSA, that sort of encryption is most likely unbreakable. The section circled in red advertises the ransom amount, in this case $300.
What To Do About Ransomware
Once infected with ransomware, the options are simple. Victims either pay up, or they don’t. Neither option is a good choice. Not paying means the files are lost. Then the user has to decide whether to scrub the computer with an anti-malware product, or rebuild the computer completely.
But paying out the ransom stinks too, because this forces victims to trust the extortionist. Before biting the bullet and paying the ransom, consider the following: Once the extortionist has the money, why send the decryption information? And, if it all works out and your files are released, you still have to go through the same process of deciding whether to scrub the computer with an anti-malware product or rebuild it.
Today's New and Improved Ransomware
Earlier, I briefly mentioned PowerLocker as the new and improved ransomware. And it has the potential to do more harm than any previous variant of ransomware. Dan Goodin at Ars Technica provided this explanation of what PowerLocker is capable of doing.
In his post, Goodin states that the digital underground has decided to go commercial, offering PowerLocker as a DIY malware kit for $100, which means that more bad people – particularly those who are not proficient in malware-speak – will be able to inflict financial pain on unsuspecting Internet travelers.
"PowerLocker encrypts files using keys based on the Blowfish algorithm. Each key is then encrypted to a file that can only be unlocked by a 2048-bit private RSA key, " Goodin writes.
I like to second source information about malware that has just been discovered, and is not yet circulating in the wild. So I contacted Marcin Kleczynski, CEO and founder of Malwarebytes.org, asking for his opinion on PowerLocker.
Kleczynski, along with his colleagues Jerome Segura and Christopher Boyd, mentioned that PowerLocker is so new that much of what’s being published is speculation. Bearing that in mind, PowerLocker potentially improves upon CryptoLocker by being able to:
- Disable certain core Windows programs, such as task manager, regedit, and command line terminal
- Start in regular and safe mode
- Evade VM detection and popular debuggers
The above improvements are all meant to make it more difficult to find and remove PowerLocker.
"Given the success of CryptoLocker, it's not surprising to see copycats coming up with better features," Kleczynski said. "The good news: since this threat was caught early, it should enable law-enforcement agencies to nail it before it gets out and starts infecting PCs."
Protecting Your Computer
So how can you protect yourself from being held ransom? Kleczynski provides some simple advice.
"Be careful when opening email attachments. In particular: Amazon, DHL, and other similar invoices that come as a zip file. More often than not these are fake, and contain malware," Kleczynski said.
Beyond that, there is no magic formula to avoid ransomware. It's just malware looking for vulnerable computers to exploit. Anti-malware programs may be of some help, but they usually kick in after the data has been encrypted. The best solution is to keep the computer’s operating system and application software up to date, eliminating any weaknesses the bad guys could exploit.